Cybersecurity's Key Objectives
The CIA and DAD Triads, and Non-repudiation are integral concepts for any aspiring cybersecurity professional to learn. Here we will talk about what they are and give some examples of their use. This content is a part of the exam objectives for the CompTIA Security+ SY0-701 exam in Domain 1.2 - Summarize fundamental security concepts.
SECURITY+CYBERSECURITY
Zachary Kivenas
9/30/20243 min read
What do you think of when you think of the word cybersecurity? If you are anything like me, it is something akin to a group of social outcasts in a dim basement, hacking corporations while loud 90s techno music is blaring in the background. Now, obviously, this isn't the case. Still, some aspects, such as hacking into systems to find vulnerabilities, patching those vulnerabilities, and hardening your systems are a part of it. This is only one part of it though, and it is important to understand the fundamentals and that there are three key objectives to any program or endeavor in cyber security. We call them the CIA triad.



The CIA Triad
Confidentiality ensures that unauthorized individuals do not have access to sensitive information. Some common methods cybersecurity professionals use to achieve confidentiality are by using security controls like firewalls, access control lists, and encryption.
Integrity ensures that information and systems are kept in the intended state and not altered, corrupted, or destroyed intentionally or unintentionally. This can be achieved with the use of hashing for example.
Availability ensures that information and systems are ready and accessible when those who are authorized to access them need to. Fault tolerance and backups are some of the ways to achieve this objective.
Cybersecurity professionals regularly refer to these three goals when considering a situation and how to handle it. Does your company handle sensitive information such as customer PII (personally identifiable information)? Then confidentiality might be a major concern for you. You could then work to ensure this confidentiality by making strict firewall rules that only allow specific traffic to the servers holding this customer information. Maybe the information is so sensitive that completely removing these databases from networks that have access to the internet is necessary. You could then ensure that all customer information is encrypted at all times, whether it be data at rest, in transit, or in use. This could also be completely overkill for your company which might not need to take confidentiality so seriously. This however is just an example of how one would use the CIA triad when assessing a system's needs. These goals are overarching and are completely dependent on your specific situation.
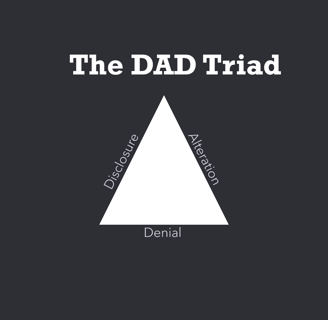
Now that we know the three key objectives of cybersecurity, it is time to take a look at the CIA triad's darker brother, the DAD triad. The DAD triad is in a sort the mirror of the CIA triad, where the CIA triad is cybersecurity's key goals, the DAD triad is cybersecurity's threats to those goals, and they map directly to each of the CIA traids component objectives.
The DAD Triad
Disclosure is the exposure of sensitive information to unauthorized individuals, also known as data loss. This principle maps directly as the threat to confidentiality and can be intentional, such as a hacker stealing PII, or unintentional, such as misconfigured permissions allowing employees to accidentally see sensitive information.
Alteration is the unauthorized modification of information and can also be intentional, from bad actors for example, or unintentional, from something like a power surge corrupting data. This threat pertains to the integrity key objective.
Denial is the disruption of service, or access to systems and information, to authorized users and stands directly opposed to the availability key objective. This can come in the form of an intentional DDoS attack, or something as simple as the loss of power due to a storm.
As you can see, all of these threats can come as the sole objectives of a threat actor. On the flip side though, all of these threats can also come from unintentional sources. What is clear, and what the DAD triad does well to put into perspective, is the sheer scale that cybersecurity and its designs have to be implemented on and all the possibilities that have to be considered as the cause of a potential threat. With threats ranging from power outages during a storm, to the typical hacker gaining access to restricted information and systems without ever being physically on-site, it's also clear that cybersecurity professionals have to be involved with far more than just computer systems.
A Bonus Objective
After going through all the corresponding threats to the CIA triad, and seeing that ill-intended threat actors could be the cause of all of them, maybe you've thought about how we tie actions to people and how important it is to be able to prove, without a reasonable doubt, that the said actions are tied to that person. This is where another very important key objective comes in called Nonrepudiation. This objective isn't a part of the CIA triad, but it is just as important nonetheless.
Nonrepudiation means that someone who performed an action or task cannot later deny that they did so. This is commonly achieved through the use of digital signatures which are used to verify that a message, for example, came from the source that is being claimed.
